Safe Computing Tips for our Clients
| To answer the ongoing demand by clients,
friends, and family for computing tips and help, we have put together
this page of guidance, tips, and recommendations to help make your
home and small office/home office computing experience easier. This
is not a complete list of help but we intend to continue to add to
it as we address various questions for our customers. For customized
support or for larger business needs, contact LRT for a complete analysis
of your business needs. |
|
How to Identify Email HOAXES and/or
URBAN LEGENDS
Every day, you receive emails that you are asked to pass
on. The contents of many of these emails are HOAXES and/or URBAN LEGENDS
that have been around for a long time, while others profess to pass on
USEFUL INFORMATION.
ALWAYS checks these things out BEFORE passing them on (and
you should too, before sending anything out). There are numerous places
on the Internet that you can use to check your facts. One good place to
check the facts is TruthOrFiction.com http://www.truthorfiction.com/
LRT Product Recommendations
As our clients hear repeatedly from LRT - always
use up-to-date Antivirus, Firewall, spyware removal software, and anti-spam
protection for business or home computing. We hear complaints daily about
the effort wasted in the battle against spammers, hackers, and virus writers.
We agree and remind you that use of the tools listed above will minimize
these threats to your computing environment.
These four tools each perform
a different function and
we recommend all computers be protected with all four.
Many solid products are available in a variety of price
ranges. LRT has no affiliation with these companies. We just like their
products and use them at home and for our friends and family. Call LRT
to discuss the right product choice for your business needs.
Our personal staff picks for home and SOHO use are
listed below.
In the US, Norton
and McAfee
Antivirus are both highly recommended.
ZoneAlarm Firewall is reliable and easy to use and understand
product. A free and a professional version are available.
MailWasher
is a powerful email checker with effective spam elimination which works
by making spammers think you no longer exist by bouncing back their email
so it looks like your address has been closed down.. A free and a professional
version are available
Visit www.cnet.com
to read user reviews of products before you purchase.
Current Alert
There is a new version of the MyDoom mass-mailing worm
in circulation on the Internet. The bogus message directs folks to click
on a link, directing them to an infected system, which then infects your
system. Some of the emails claim to be from PayPal, the online payment
system that is part of Ebay. Typical bogus message content would be something
like: "Congratulations! PayPal has successfully charged $ 175 to your
credit card. Your order tracking number is A866DEC0, and your item will
be shipped within three business days. To see details, please click this
link." Of course, understanding that you did not authorize PayPal to do
anything to your credit card, curiosity might lead you to click on the
link to see if someone is ripping you off. It pays to be cautious, if
you use PayPal, instead of clicking on that link (which will more than
likely deliver you a "surprise" package), just contact PayPal directly
and see if anything has actually happened.
There are many things you can do to protect your system, but the biggest
three are: Be suspicious, if you did not do anything, or request anything,
check things out before just clicking away - always check to see if there
is water in the pool BEFORE diving in. This is true of non-requested email
attachments, emails themselves (no, I am afraid you did not win that lottery
- no, you are not a large bank capable of transferring millions of dollars,
and no, there is no free lunch). Keep your anti-virus software up to date
and run a good firewall. Use Windows Update frequently at home - Microsoft
has been very, very busy the past two months and you do not have the push
technologies at home that we have here. It pays to check for anything
that Microsoft describes as "critical", a term they are not kidding about.
Compute wisely - compute safely.
----------------------------------------------------------------------------------------------
A competition between computer-virus writers is responsible
for more than a dozen recent variants of the Mydoom, Netsky and Bagle
viruses in the past week. That includes the most recent, W32/Bagle.j@MM,
another Medium Risk mass-mailing worm with characteristics similar to
its predecessors—including a potentially dangerous backdoor component.
Caution: An infected email can
come from addresses you recognize.
What to look for:
From: Varies. Address may be forged.
Subject: Varies. Examples— - E-mail account security warning.
- Notify about using the e-mail account. - Warning about your e-mail
account.
Body: Varies. Example— Dear user of "(user's domain inserted*)"
mailing system, Your e-mail account will be disabled because of improper
using in next three days, if you are still wishing to use it, please,
resign your account information. For details see the attached file.
For security purposes the attached file is password protected. Password
is "(5 random numbers inserted)".
The Management, The (user's domain inserted*) team http://www.(user's
domain inserted*).com * Where the user's domain is chosen from the To:
address. For example the user's domain for user@mail.com would be "mail.com".
Attachment: File may be .EXE .PIF or .ZIP
Symantec Security Response encourages
all users and administrators to adhere to the following basic security
"best practices":
- Turn off and remove unneeded services. By default, many operating
systems install auxiliary services that are not critical, such as an
FTP server, telnet, and a Web server. These services are avenues of
attack. If they are removed, blended threats have less avenues of attack
and you have fewer services to maintain through patch updates.
- If a blended threat exploits one or more network services, disable,
or block access to, those services until a patch is applied.
- Always keep your patch levels up-to-date, especially on computers
that host public services and are accessible through the firewall, such
as HTTP, FTP, mail, and DNS services.
- Enforce a password policy. Complex passwords make it difficult to
crack password files on compromised computers. This helps to prevent
or limit damage when a computer is compromised.
- Configure your email server to block or remove email that contains
file attachments that are commonly used to spread viruses, such as .vbs,
.bat, .exe, .pif and .scr files.
- Isolate infected computers quickly to prevent further compromising
your organization. Perform a forensic analysis and restore the computers
using trusted media.
- Train employees not to open attachments unless they are expecting
them. Also, do not execute software that is downloaded from the Internet
unless it has been scanned for viruses. Simply visiting a compromised
Web site can cause infection if certain browser vulnerabilities are
not patched.
LRT Email Tips
How to Change the Program That Automatically
Starts When you Click on a Certain File Extension
This question arises usually after someone installs a new program and
now many file types now open in it instead of the program they previously
opened in. You probably have installed some program such as QuickView
which took over various file types as its own. This means they open up
in Quick view (or whatever) by default instead of the old program as you
used to see. You can change this if you want.
This is a handy instruction to keep on file
To change which program starts when you open a file In My Computer or
Windows Explorer, on the View menu, click Folder Options. Click the File
Types tab. (I only get File Types tab in My computer window)
In the list of file types, click the one you want to change. (i.e. *.pdf)
Click Edit. (see picture)
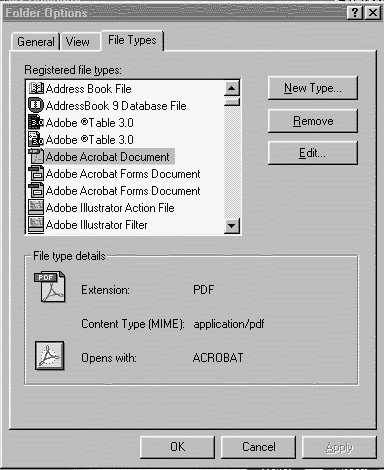
In Actions, click Open. Click Edit. In Application used to perform action,
enter the program you want to use to open files that have this extension,
and then click OK. (See Picture below)
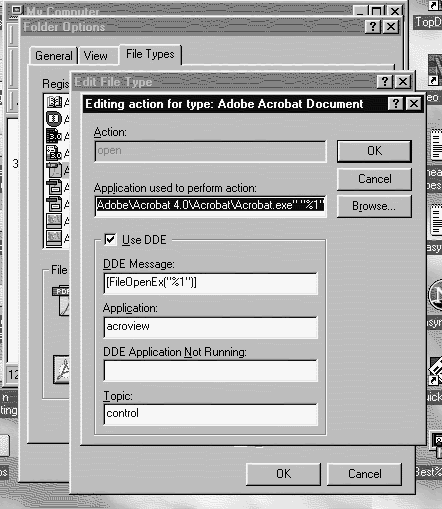
Note The settings for selected file types are shown in File type details.
OR
Windows 98 Steps:
1. RIGHT click on "Start " button & select "Explore" option.
2. In Explorer, Click on "Tools" then on "Folder Options"
3. In the Folder Options Window - select the "File Types" Tab
4. Scroll down until you come to the file type you want to change (ex.
JPEG) and click on it.
5. Choose EDIT
6. New window opens - Choose Edit again. Use Browse to move to the .exe
of the program you want to use to open this file type. E.G. "c:\program
files\photoshop\photoshop.exe"
7. Choose close.
8. That file type should open with the new program.
(Option 2 - Say you want stuff to open with Photoshop - Reinstall Photoshop
and when it asks which file types it should open - check each that you
desire.) Now I tell you.
Image Adjustment Tips
When emailing an image from a digital camera - it often becomes a 21inch
wide, low resolution attachment. Here is a trick to resize AND improve
image quality.
1. Open image in an image manipulation program such as Paint Shop Pro
or Photoshop.
2. NOTE: STEP ORDER IS IMPORTANT. First, change Resolution to 300 dpi
[it was probably only 72 dpi] in the original file. Now while on the same
screen, change image size to a standard photo size such as 4 x 6 or 8
x 10.
Note if you change size first it does not do the same thing
and image gets very jagged & hard to read - esp text!
If you don't like the new size - use File, Revert - then do image size
again. This maintains image quality much better than repeated, consecutive
image re-sizing.
3. Don't forget to SAVE the result.
Tips on How to Spot a Dangerous E-Mail
Since I get the pleasure of helping several folks recover their PC's
after they get a virus etc. I thought I would send out an explanation
of a new email scam/virus attempt that is going around and some general
tips to spot dangerous emails.
Basically, someone spoofed (i.e. pretended to be) my internet service
provider and wrote an email that was supposed to look plausible enough
to get me to open the (virus or trojan infected) attachment. There are
several variations of this. Two are shown below:
----------------------------------------------------
Version 1
Dear user of Siscom.net gateway e-mail server,
Our antivirus software has detected a large ammount of viruses outgoing
from your email account, you may use our free anti-virus tool to clean
up your computer software. For more information see the attached file.
Have a good day,
The Siscom.net team
Version 2
Dear user of "Siscom.net" mailing system,
Some of our clients complained about the spam (negative e-mail content)
outgoing from your e-mail account. Probably, you have been infected
by a proxy-relay trojan server. In order to keep your computer safe,
follow the instructions. For details see the attached file. For security
reasons attached file is password protected. The password is "28315".
Have a good day,
The Siscom.net team
---------------------------------------------------
Watch out for any email you weren't expecting that tries to persuade
you to open an email attachment.
However, the clues that alerted me are listed below so you can know what
kind of things to look for. Basically - be very cautious of any attachment
- even if it comes from your ISP. Having current anti virus with automatic
updates and a firewall will prevent almost all viruses or worms from entering
your system. This frustrates the writers of these things so they try now
to trick you into taking an action -- like opening an infected file --
that will cause your pc to become infected.
So here's the clues:
1. An ISP or company like Microsoft would post a patch etc. on their
web site - not email it to you. NOTE: Microsoft NEVER e-mails people.
Windows has a feature that lets it check the microsoft web for updates
automatically. Also a bank, PayPal, Ebay, and most reputable online businesses
will never send you an emailed form requesting "an update of your
account record" - Especially one that requests security information
like "Pin", "Password", "Account Number"
etc.
2. The first attachment was a ".zip" file and the second was a ".pif"
file. Never trust a ".pif" file. As for ".zip" files - they can contain
anything.
3. The password offered for opening the ".zip" file "for security purposes"
..... well -- if its included in the same email as the file - it offers
no security whatsoever.
4. Typos - Actually typos are a big clue of spam, viruses, etc. I don't
know why people that are smart enough to come up with a scam or virus
cannot figure out how to use a spell checker.
5. One of the e-mails referred to a return email address of "staff@siscom.net"
which did not work when I tried it directly.
6. On the ISP web site itself - there was no message related to the contents
of the email. If they were actually doing something as suggested in the
email - they would have had a prominent message on their web.
Happy & Safe Computing from LRT
|